
Product type
Networking | Communications Hardware | Protocols | I/O
Product
Floodgate Firewall
Product Summary
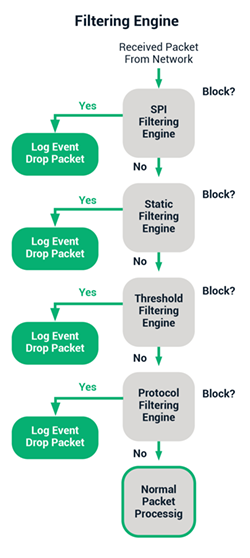
The Sectigo Icon Labs™ Embedded Firewall is a complete embedded firewall providing multiple types of filtering protecting against Internet-based threats:
- Static/rules-based filtering blocks packets based on configurable rules
- Dynamic filtering/stateful packet inspection (SPI) blocks packets based on connection state
- Deep packet inspection for industrial automation protocols allowing control and validation of each individual field within the message, and filtering of messages based on message type, contents and message source
- Threshold-based filtering blocks packets based on threshold crossings to protect against denial of service (DoS) attacks, broadcast storms and other packet flood conditions
Configurable Filtering Policies
Uses configured filtering rules to control the filtering engine. The rules provide complete control over the type of filtering performed and the specific criteria used to filter packets. Rules can be configured for:
- Static filtering rules for IP address, MAC address, port number and protocol number
- Blacklist and whitelist filtering modes
- DPI filtering rules for message type, message contents and message source
- Threshold-based filtering criteria
- Independently enable and disable static filtering, dynamic filtering, DPI filtering and threshold-based filtering
- With Floodgate Agent, configuration can be performed remotely with an enterprise security management system
EDSA Compliance Support
Provides an important building block for achieving EDSA compliance for embedded devices and provides support for the following capabilities mandated by EDSA-311:
- Protocol fuzzing attack protection
- Data flooding protection
- Denial of service protection
- Notification of attacks
- Disabling of unused ports
Logging and Alerting
Maintains a log of security events and policy violations. Changes to firewall policies are also recorded in the logs enabling support for command audit requirements. Event logs can be used for forensic investigation to determine the source of an attack.
Management System Integration
The embedded firewall is integrated with the Sectigo Agent, enabling remote management from an enterprise security management system or to other Security Information and Event Management (SIEM) systems.
This integration provides:
- Centralized management of security policies
- Situational Awareness and device status monitoring
- Event management and log file analysis
Intrusion Detection and Prevention
Hackers attempting to penetrate an embedded device using remote attacks will probe the device for open ports and weaknesses. Blocking all unused ports and protocols limits the attack surface potential hackers can exploit. Logging packets that violate configured filtering rules enables detection of unusual traffic patterns, traffic from unknown IP address or other suspicious behavior.
Supported Green Hills Products
Supported Processor Architectures
- Processor-independent
Company Headquarters
Sectigo Limited Headquarters
5 Becker Farm Road
Roseland, NJ 07068
United States


